
You’re one information breach away from having your whole on-line life turned the other way up. The issue is passwords, that are hopelessly fragile methods to safe beneficial assets.
Do not be lulled right into a false sense of safety by the idea that creating an extended, extra advanced, harder-to-guess password will in some way make you safer on-line. You may create a password that’s so lengthy and sophisticated it takes you 5 minutes to kind, and it’ll do nothing to guard you if the service the place you utilize that password shops it improperly after which has their server breached. It recurrently occurs.
Additionally: Greatest VPNs • Greatest safety keys • Greatest antivirus
And even with cheap insurance policies in place (complexity, modified recurrently, not reused), individuals are nonetheless the weakest hyperlink within the safety chain. Social engineering can persuade even clever folks to enter their credentials on a phishing website or give them up over the telephone.
The answer is two-factor authentication, or 2FA. (Some companies, being sticklers for element, name it multi-factor authentication or two-step verification, however 2FA is probably the most extensively used time period, so that is the nomenclature I’ve chosen to make use of right here.)
A 2019 report from Microsoft concluded that 2FA works, blocking 99.9% of automated assaults. If a service supplier helps multi-factor authentication, Microsoft recommends utilizing it, even when it is so simple as SMS-based one-time passwords. A separate 2019 report from Google provided related conclusions.
On this article, I reply among the most typical questions folks ask me about 2FA.
How does 2FA work? Is not it inconvenient?
Turning on 2FA for a service modifications the safety necessities, forcing you to supply at the least two proofs of id when accessing a safe service for the primary time on an unknown system. After you efficiently meet that problem, you often have the choice to categorize the system as trusted, which signifies that 2FA requests must be comparatively uncommon on the gadgets you utilize recurrently.
These two types of authentication can come from any mixture of at the least two of the next parts:
- “One thing ,” equivalent to a password or PIN
- “One thing you might be,” equivalent to a fingerprint or different biometric ID
- “One thing you’ve got,” equivalent to a trusted smartphone that may generate or obtain affirmation codes, or a hardware-based safety system
For probably the most half, the two-factor authentication methods you see in place as we speak use the primary merchandise (your password) and the final merchandise (your smartphone). Smartphones have turn out to be ubiquitous, making them superb safety gadgets.
Your smartphone can help with authentication by offering a singular code that you simply use alongside together with your password to sign up. You may purchase that code in certainly one of two methods: Despatched as a textual content message from the service, or generated by an app put in in your telephone. (Some companies additionally let you approve a push notification in your smartphone.)
The dialog field proven right here, for instance, is what I noticed moments in the past after I tried to sign up to my Gmail account from a browser I had by no means used earlier than
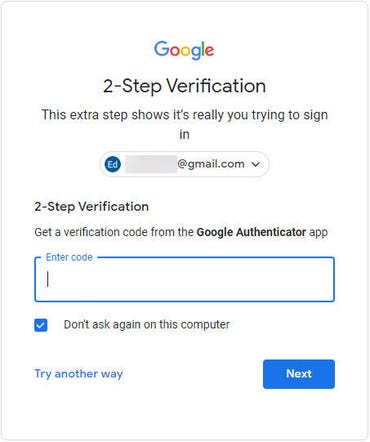
If somebody tries to sign up to an account protected by 2FA, they will want a second proof, such because the code from an authenticator app
If this sign-in request have been from somebody who had stolen my Google account credentials, they’d be stopped lifeless of their tracks. With out that code, they can not proceed the sign-in course of.
Most (however not all) companies that help 2FA supply a alternative of authentication strategies. Google and Microsoft, for instance, can each push notifications to a trusted system; you faucet the notification to approve the sign-in. An growing variety of companies help the usage of {hardware} safety keys (see: “YubiKey hands-on: {Hardware}-based 2FA is safer, however be careful for these gotchas.”)
And, in fact, most companies supply the choice to print out backup restoration codes, which you’ll retailer in a secure place and use within the occasion your normal secondary authentication technique is unavailable. In case your smartphone is misplaced, stolen, or broken, you will want these codes.
Which authentication technique is greatest?
The perfect authentication technique is the one you are most comfy with. Simply be sure you have at the least two choices, to keep away from the chance of being locked out of your account.
I favor the choice to make use of an authenticator app moderately than receiving codes through textual content message every time potential, and so do you have to, for 2 good causes. The primary is a matter of easy logistics. There are occasions when you’ve got entry to the web (through a wired connection or Wi-Fi) however cannot obtain a textual content message, as a result of your mobile sign is weak or nonexistent, otherwise you’re utilizing a special SIM whereas touring. The second is the small however actual likelihood that an attacker will social-engineer their means via your cell service’s defenses to accumulate a SIM card together with your telephone quantity, a course of known as “SIM-jacking.”
The most well-liked 2FA app is Google Authenticator, which is obtainable on iOS and Android. However there are many options; as a result of the method for producing safe tokens relies on open requirements, anybody can write an authenticator app that performs the identical operate. Actually, you need to use a number of authenticator apps. I take advantage of Microsoft Authenticator, which is able to receiving push notifications from private and enterprise accounts on Microsoft’s platforms, in addition to 1Password, which integrates 2FA help into the identical app that manages passwords, making sign-in much more seamless. I additionally suggest the third-party app Authy, which lets you handle authenticator codes on a number of gadgets with the flexibility to again up and restore account settings. (For particulars, see “Shield your self: How to decide on the appropriate two-factor authenticator app.”)
It is value noting that establishing an account in your authenticator app solely requires an information connection throughout the preliminary configuration. After that, every little thing occurs in your system. The method is ruled by a well-accepted customary that makes use of the Time-based One-Time Password algorithm (TOTP). That algorithm makes use of the authenticator app as a complicated calculator that generates codes utilizing the present time in your system and the shared secret. The web service makes use of the identical secret and its personal timestamp to generate codes that it compares towards your entry. Either side of the connection can regulate for timezones with out drawback, though your codes will fail if the time in your system is improper.
How do I do know which companies help 2FA?
After I began writing about this know-how a decade in the past, 2FA help was comparatively uncommon. As we speak, it is commonplace.
Google accounts, together with each shopper Gmail and enterprise Google Workspace accounts, supply a variety of two-step verification options. All Microsoft accounts, together with the free accounts used with Outlook.com, Xbox, Skype, and different shopper companies, help a wide range of authentication choices, as do the Azure Lively Listing accounts used with Microsoft’s enterprise and enterprise companies, together with Microsoft 365 and Workplace 365.
2FA help is ubiquitous amongst social media companies (Fb, Twitter, Instagram, and so forth). Each on-line storage service value contemplating helps 2FA, as do most area registrars and internet hosting corporations. In case you’re uncertain a few particular service, one of the best place to test is an excellent open supply data repository known as the Two Issue Auth Checklist. And if a high-value service you depend on does not help 2FA, effectively, possibly you must contemplate switching to at least one that does.
Which companies ought to I shield first?
You most likely have login credentials at dozens of on-line companies that help 2FA, so one of the best technique is to make a prioritized checklist and work your means via it. I counsel these priorities:
- Password/id managers. Utilizing a password supervisor is probably a very powerful means to make sure that you’ve got a powerful, distinctive password for each service, however that additionally creates a single level of assault. Including 2FA shores up that potential weak point. Notice that for some password administration software program, 2FA help is a paid possibility.
- Microsoft and Google accounts. In case you use companies from both firm, including 2FA help is important. Happily, it is also simple.
- E mail accounts. If a foul actor can take over your e-mail account, they will usually wreak havoc, as a result of e-mail messages are an ordinary technique of sending password reset hyperlinks. Messages despatched from a compromised e-mail account can be used to assault your folks and associates (by sending malware-laden attachments, for instance). In case you use Outlook.com, Alternate On-line, Gmail, or G Suite, your e-mail account makes use of the id verification technique related together with your Microsoft or Google account. In case you use a special e-mail service, you will must arrange 2FA individually.
- Social media accounts. As with e-mail, the largest danger related to a hacked Twitter or Fb account is that it is going to be used towards your folks and associates. Even in the event you’re a lurker who hardly ever posts something on social media, you must shield these accounts.
- Banks and monetary establishments. Most banks and bank card corporations have made important investments in back-end fraud detection packages, which is why 2FA choices are sometimes restricted in contrast with different classes. Nonetheless, it is value exploring these settings and tightening them as a lot as potential.
- Buying and on-line commerce. Any website the place you have saved a bank card quantity must be secured.
How do I arrange 2FA?
Organising extra safety for many on-line companies requires minimal technical abilities. If you need to use your smartphone’s digicam, kind a six-digit quantity, and faucet OK in a dialog field, you’ve got all the talents required. Essentially the most tough a part of the job is discovering the web page that has the related settings.
In case you’re utilizing SMS messages, all you could do is affiliate a cell phone quantity together with your account. (It’s also possible to use a digital telephone line, equivalent to a Google Voice quantity, that may obtain SMS messages.) Configure the account to ship a code to that quantity everytime you sign up on an untrusted system. For instance, here is what this selection appears like when enabled on a Twitter account:
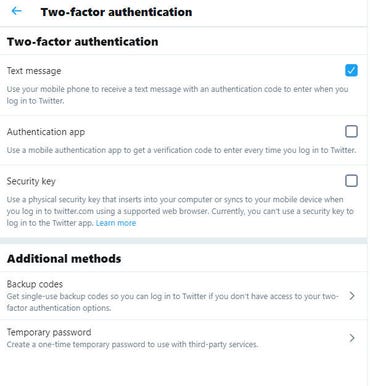
The only 2FA possibility is a code, despatched through SMS message to a registered telephone. That is the 2FA setup web page for Twitter.
Organising 2FA on a Twitter account requires you to first re-enter your password after which enter the telephone quantity the place you need to obtain authentication codes. After you full that course of, you will obtain a code on that system. Enter the code to verify you acquired it, and the 2FA setup is full. Helpfully, Twitter mechanically generates a restoration code on the finish of this setup course of; print it out and file it in a secure place so you may get better within the occasion your major 2FA technique now not works.
To get began with an authenticator app, you first want to put in the app on the cell system you need to use as your second authentication issue:
- In case you carry an iOS system, you will get the Google Authenticator app from the App Retailer. (It is optimized to be used on iPhones however ought to work on an iPad as effectively.) On Android gadgets, set up the Google Authenticator app from the Google Play Retailer.
- The Microsoft Authenticator app, which makes use of the identical customary to create authentication tokens, is obtainable for Android gadgets from the Google Play Retailer and for iOS gadgets from the App Retailer.
- Twilio Authy can also be accessible from the App Retailer and from the Google Play Retailer.
- In case you use the LastPass password supervisor, observe these directions to put in the LastPass Authenticator app, which is designed to work with the LastPass app on cell gadgets and the desktop.
- In case you use 1Password as your password supervisor, 2FA help is constructed into the 1Password app on all platforms. For particulars on find out how to use the One-Time Password characteristic, see this 1Password help web page.
After you put in the app to your system, the following step is to set it as much as work with every account the place you’ve got enabled 2FA.
Additionally:
Make your cloud safer: Find out how to allow two-factor authentication for the most well-liked cloud companies.
The setup course of sometimes requires that you simply enter a shared secret (an extended textual content string) utilizing the cell app. All the cell apps I listed above help utilizing a smartphone digicam to take an image of a QR code, which incorporates the shared secret to your account. That is a lot simpler than coming into a posh alphanumeric string manually.
Right here, for instance, is the QR code you will see when establishing a Dropbox account:
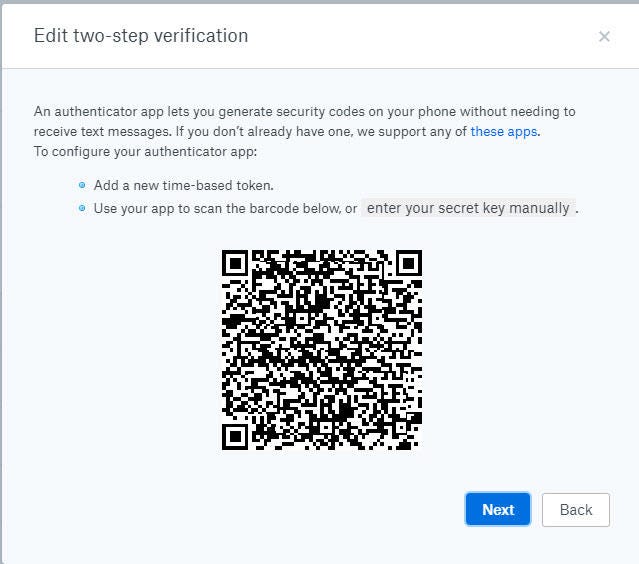
In your smartphone app, select the choice so as to add a brand new account after which snap an image of the bar code to mechanically arrange 2FA help.
In your authenticator app. select the choice so as to add a brand new account, select the bar code possibility, intention the smartphone on the bar code in your laptop display, and look ahead to the app to fill within the obligatory fields.
After you arrange the account within the authenticator app, it begins producing codes primarily based on the shared secret and the present time. To finish the setup course of, enter the present code from the authenticator app.
The following time you attempt to sign up with a brand new system or internet browser, you will must enter the present code, as displayed by the authenticator app.
In case you use older e-mail apps that do not help trendy authentication with an account that is protected by 2FA, your regular password will not work anymore. You may must generate particular passwords to be used completely with these apps. The safety settings to your account ought to information you thru that course of. (However actually, if you’re utilizing an app that is so outdated it requires an app password, you must change it with a contemporary various.)
As a part of the 2FA setup course of, you must also generate a number of restoration codes, which you’ll print out and retailer in a secure place. Within the occasion your smartphone is misplaced or broken, you need to use these codes to regain entry to your account.
How do you switch 2FA accounts to a brand new smartphone?
In case you use SMS textual content messages as a second issue for authentication, transferring your quantity to the brand new telephone will seamlessly switch your 2FA setup too.
Some authenticator apps let you generate codes on a number of gadgets. 1Password and Authy each fall into this class. Arrange the app on the brand new telephone, set up the app, sign up, after which test every account to verify that the codes generated on the brand new telephone work correctly. Microsoft Authenticator permits you to again up codes to the cloud and restore them on a brand new system. For directions, see “Again up and get better account credentials within the Authenticator app.”
For Google Authenticator and different no-frills apps, nevertheless, you will must manually re-create every account on the brand new system. Set up the authenticator app in your new system and repeat the setup course of for every account you used together with your previous telephone. Organising an account on a brand new authenticator app mechanically disables codes generated by the previous system.
Two-factor authentication will cease most informal assaults lifeless of their tracks. It isn’t excellent, although. A decided attacker who’s immediately concentrating on a selected account would possibly have the ability to discover methods to work round it, particularly if they will hijack the e-mail account used for restoration or redirect telephone calls and SMS messages to a tool they management. But when somebody is that decided to interrupt into your account, you’ve got an even bigger drawback.
Any questions? Ship me a be aware or go away a remark beneath.