Safety and threat leaders beware, the Biden Administration launched the subsequent main step in its plan to implement the Nationwide Cybersecurity Technique (NCS) on July 13, 2023. The Nationwide Cybersecurity Technique Implementation Plan (NCSIP) contains 65 federal initiatives throughout 5 pillars geared toward growing cybersecurity funding, assigning federal businesses to particular initiatives, and giving timelines for completion.
Eighteen federal departments and businesses are tapped to steer initiatives, with the Workplace of the Nationwide Cyber Director (ONCD), Cybersecurity and Infrastructure Safety Company (CISA), Nationwide Institute of Requirements and Expertise (NIST), Division of Protection, Division of Justice, Division of State, Deparmtent of Homeland Safety, and the FBI getting the lion’s share of the duty. The ONCD and Workplace of Administration and Finances (OMB) will lead the administration’s efforts and make funding proposals. The plan, nonetheless, doesn’t embody any funding however does reference future finances requests such because the Administration Cybersecurity Priorities for the FY 2025 Finances.
The NCSIP is the implementation plan for the NCS, offering extra particulars on the timeline, tips on how to execute it, and what entity will probably be answerable for executing it. To study extra in regards to the NCS and every initiative in depth, learn our earlier weblog on the announcement right here.
The NCSIP is supposed to do two issues:
- Be certain that the private and non-private sector tackle cyber dangers towards essential infrastructure.
- Present incentives for these dedicated to long-term cybersecurity investments.
Notably, every pillar has initiatives that instantly have an effect on the non-public sector, encompassing any and all “essential infrastructure.” Use The Forrester Mannequin To Defend Towards Nation-State Threats to know your potential legal responsibility to rules like these and what to anticipate within the subsequent a number of years.
Under is a fast overview of every pillar, together with its key initiatives. Every key initiative signifies whether or not the non-public sector or federal authorities will probably be accountable or affected.
Pillar One: Defend Vital Infrastructure
Pillar One establishes rules, requirements, and directives to assist the protection of essential infrastructure — it’s the place rules meet essential infrastructure suppliers in the private and non-private sector. It focuses on baseline requirements for essential infrastructure, creating a way to offer updates and knowledge to essential infrastructure suppliers, and modernizing federal cybersecurity infrastructure via tabletop workouts, unification of federal cyber facilities, and the modernization of the Federal Civilian Government Department.
Pillar Two: Disrupt And Dismantle Menace Actors
Pillar Two is as near “hack again” as we are going to doubtless get — coordinating the disruption of cyberattacks via as many means as attainable by the federal authorities. It contains takedown campaigns, ransomware disruption, laws, proposals for rules on infrastructure-as-a-service suppliers, worldwide relations, and updates to worldwide requirements.
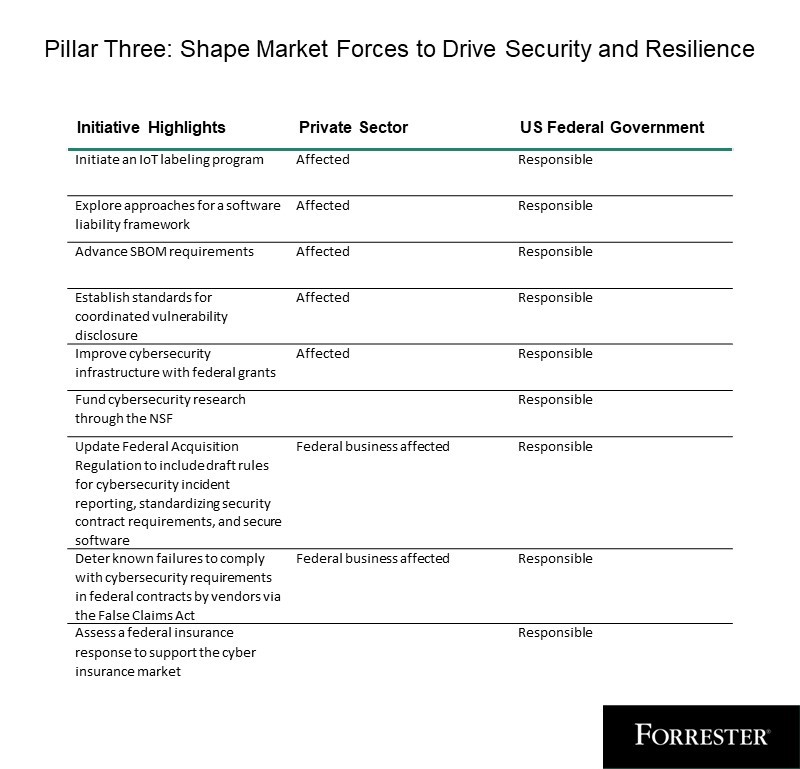
Pillar Three: Form Market Forces To Drive Safety And Resilience
Pillar Three continues the federal government’s emphasis on securing the software program provide chain by advancing software program invoice of supplies (SBOM) necessities, initiating internet-of-things labeling, and establishing requirements for coordinated vulnerability disclosure. For extra on SBOM, try Janet Worthington’s report, Put together For Regulatory Necessities On Software program Payments Of Supplies.
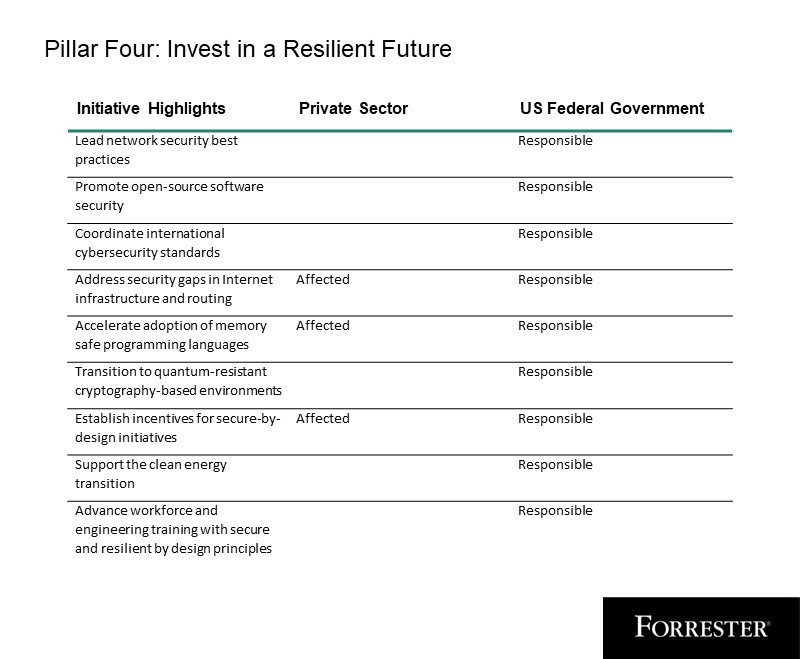
Pillar 4: Make investments In A Resilient Future
Pillar 4 seems to the longer term — securing the web and the workforce towards rising applied sciences. It focuses on enhancing the safety of the web, transitioning to safer applied sciences corresponding to memory-safe programming languages and quantum-resistant cryptography-based environments, and enabling initiatives like secure-by-design and engineering coaching to blossom.
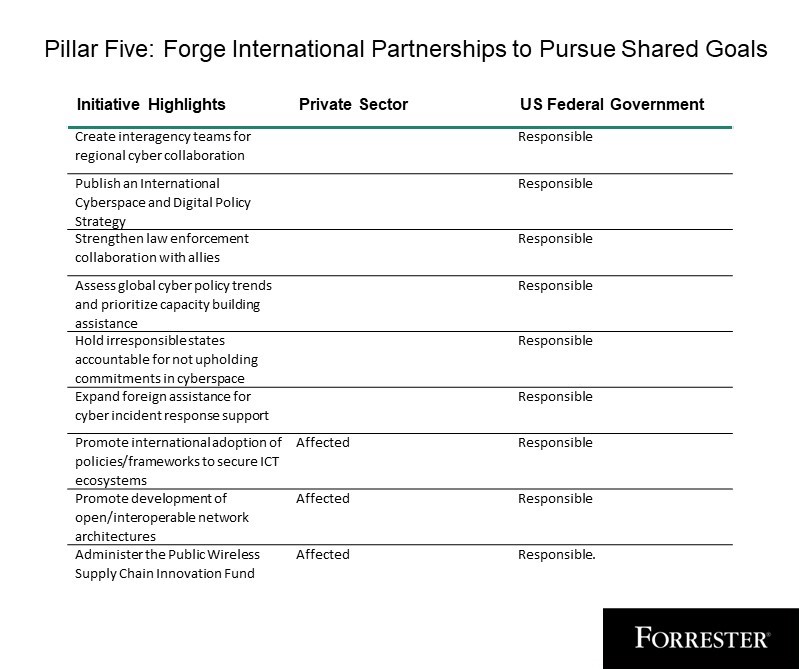
Pillar 5: Forge Worldwide Partnerships To Pursue Shared Objectives
Pillar 5 focuses on enhancing cybersecurity capabilities, requirements, and help with US allies and companions to safe our on-line world. With its worldwide partnerships, the US authorities will construct cyber coalitions and capability, strengthen regulation enforcement, maintain states accountable, develop overseas help for incident response, and promote safe provide chains for data and communications applied sciences.
The NCS and NCSIP have the potential to bolster the US’ cyber resilience. This management on the nationwide stage has been lengthy wanted given the fractured nature of US cyberdefense and the reliance of personal sector entities to defend themselves towards nation-state actors.
Whereas these are optimistic steps, these initiatives will push extra regulation to the non-public sector, particularly essential infrastructure. Safety and threat leaders should plan for and adapt to those modifications as they’re launched.
Keep tuned for added blogs and analysis because the NCS strikes ahead. Forrester purchasers can schedule an inquiry or steering session to debate any of the matters talked about on this weblog and the way they might influence them.
We’re excited to announce that we’re accepting entries for The Safety & Danger Enterprise Management Award! This is a wonderful alternative to showcase how your group builds belief and to realize recognition to your efforts. We will’t wait to see how you’ve gotten remodeled safety, privateness, and threat administration to drive trusted relationships with prospects, staff, and companions to gas your group’s long-term success.
The deadline for submissions is Friday, August 11. To view full award nomination standards and submit an entry, go to right here.


